eC Guard
Secure Communication Wherever You Are
For business trips abroad
For businesses with high security requirements

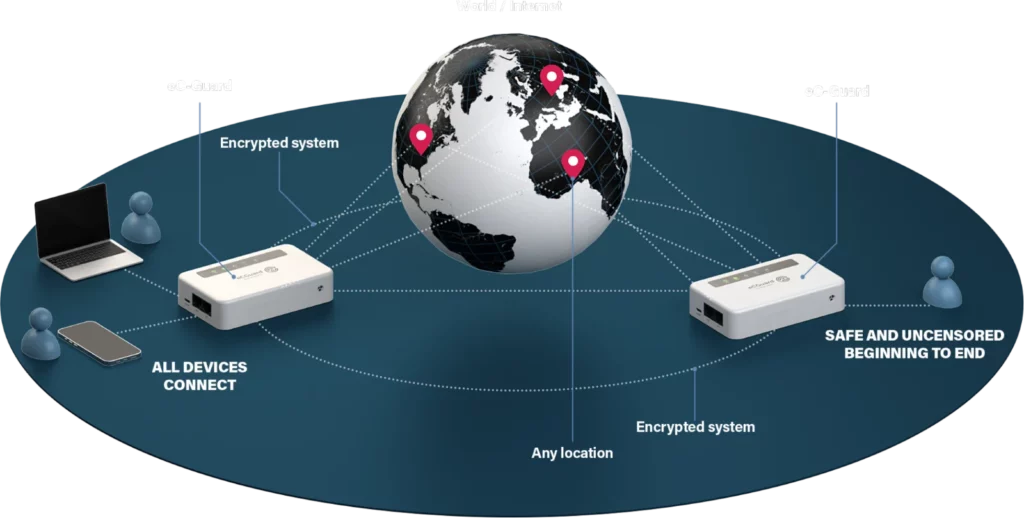
Flexible and User-Friendly Solution for Various Needs
eC Guard is designed to protect both smartphones and computers, with connections via WiFi or network cable.
Choose between desktop units for multiple users or discreet smartphone-sized devices—perfect for your handbag or jacket pocket.
By placing eC Guard between the internet and your devices, secure communication is enabled while preserving your privacy.
All communication is encrypted through a VPN tunnel, and your devices are never exposed online, allowing you to work safely and securely with ease
What can eC-Guard do for you and your organization?
- eC-Guard ensures the protection of communication from all devices, including computers, smartphones, and other digital equipment
- With eC-Guard, digital devices are never directly exposed to public networks
- By using eC-Guard for communication and security, your organization is better positioned to meet the requirements of GDPR and NIS2 directives
- eC-Guard is an ideal solution for protecting and providing access to Operational Technology(OT) devices. It extends the lifespan of OT devices that have reached end-of-life or have outdated security features
- eC-Guard’s flexible design allows its security features to either protect communication and devices, or for secure hardened devices conceal the communication

Design Principles and Key Features
eC-Guard is designed to be available on a variety of hardware platforms to meet different environments and needs. This includes desktop devices for multiple users in office environments as well as discreet, smartphone-sized units. Additionally, eCiceron offers customers the option to have eC-Guard implemented on specialized, custom platforms.
Furthermore, eC Guard is designed with flexibility to support various VPN technologies, aimed at accommodating different use cases and environments. eC Guard has the capability to both conceal and protect devices and communication.
By designing eC-Guard as an independent, mobile standalone device, several advantages are achieved:
- eC-Guard ensures that all communication is encrypted by being placed between public networks and the user’s devices.
- As a standalone device, eC-Guard also functions as a firewall, protecting connected devices from intrusion attempts.
- All digital devices, regardless of their operating system, that can connect via Wi-Fi or Ethernet can be protected by eC-Guard.
- Through its architecture with specific software designed to minimize the footprint, eC-Guard reduces attack surfaces and potential vulnerabilities.
- eC-Guard supports various VPN technologies that can be selected based on specific needs and use cases.
- The protection provided by eC-Guard is unaffected by software updates to the users’ devices.

When to use eC Guard
If you are using a standard smartphone, tablet, or laptop:
- With eC Guard, you can securely connect to your organization’s network via VPN, ensuring that all your communications are encrypted.
- If a VPN client is already installed on your devices, eC Guard can act as a firewall, adding an extra layer of protection. It can also be used to either enhance your traffic security with an additional VPN layer or conceal the VPN traffic from the client.
- When traveling abroad, connect eC Guard to the local mobile network or Wi-Fi. By doing so, your devices will not be exposed on the network, and all traffic to your home network will be encrypted through the VPN.
Using a hardened and secure smartphone or laptop:
- eC Guard manages VPN-blocking firewalls that can prevent VPN traffic from secure devices.
- eC Guard conceals VPN connections, including the IP address of the receiving VPN server.
- By connecting through eC Guard, metadata is protected, and traffic pattern analysis is made more difficult.
- When traveling abroad, connect eC Guard to the local mobile network or Wi-Fi. By doing so, your devices will not be exposed on the network, and all traffic to your home network will be encrypted through the VPN.

What does eC Guard offer that a VPN client does not?
- eC Guard provides an always-on VPN that guarantees encryption of all network traffic,without exceptions.
- A VPN client encrypts the traffic that the operating system directs to it, meaning you must trust both the operating system and the VPN client’s implementation.
- As a separate device, eC Guard also functions as a firewall, protecting connected devices from intrusion attempts.
- While a VPN client is designed to encrypt outbound and inbound traffic, it is not a firewall and does not provide intrusion protection.
- When eC Guard connects to the network via mobile data or Wi-Fi, the devices connected to it will not be exposed to the local network, nor will their IMEI numbers be registered on mobile towers
- When using a VPN client, you must first connect your device to a Wi-Fi or mobile networkbefore the VPN tunnel can be established.
- As a standalone VPN device, eC Guard can either secure communication using VPN or obfuscate/conceal network traffic from the connected devices using VPN-services.
- Connecting a VPN client on a laptop or smartphone to a public VPN-service is not recommended as the VPN makes the laptop or smartphone an extension of that network
What VPN technologies do eC Guard support?
eC Guard is designed as a platform capable of supporting various VPN technologies, selected based on the specific needs, environment, and desired functionality.
We advocate for well-established technologies, transparency, and open standards. By closely following developments in this field, we ensure that our customers receive the best recommendations for making each project successful.
Prometheus and Grafana implemention
By integrating with Prometheus and Grafana, we can enhance your ability to collect statistical data for future decision-making and life cycle analysis.
Prometheus is a powerful monitoring and alerting toolkit that allows you to gather and store time-series data related to the performance and health of your systems. Grafana complements Prometheus by providing a robust visualization platform, enabling you to create interactive and informative dashboards. grafpana.
Cisco Umbrella, enhance the protection of your assets
Cisco Umbrella is a powerful cybersecurity tool, and its integration with eC-Guard can enhance the protection of your assets. You have the flexibility to monitor it independently or integrate it seamlessly into your eCiceron’s Strategic Awareness Cell, a MDR service with highly skilled personnel.
By combining Cisco Umbrella and eC-Guard, you can strengthen your organization’s security posture, safeguarding your digital assets from threats such as malware, phishing attacks, and malicious websites. This integration provides you with the capability to actively monitor and respond to security events, ensuring the safety and integrity of your network and data.

Inhouse developed User Interface for optimized experience and usability
Cisco Umbrella is a powerful cybersecurity tool, and its integration with eC-Guard can enhance the protection of your assets. You have the flexibility to monitor it independently or integrate it seamlessly into your eCiceron’s Strategic Awareness Cell, a MDR service with highly skilled personnel.
By combining Cisco Umbrella and eC-Guard, you can strengthen your organization’s security posture, safeguarding your digital assets from threats such as malware, phishing attacks, and malicious websites. This integration provides you with the capability to actively monitor and respond to security events, ensuring the safety and integrity of your network and data.
Technical specifications
Hardware
The hardware specifications listed below represent one of our most popular end-user devices. This hardware is well-suited for the busy remote worker due to its extended battery life and integrated LTE modem, providing reliable connectivity on the go.
| Hardware Spec | |
|---|---|
| CPU | QCA9531, 650 MHz SoC |
| RAM | DDR2 128 MB |
| Storage | 16 MB NOR + 128 MB NAND |
| SIM type | Nano SIM card |
| Ethernet | 1 Gbit |
| Speed | 300 Mbit/s Wi-Fi speed |
| SD memory | 512 GB Max MicroSD |
| Battery | Built-in 5000 mAh |
| Dimensions | 120x74x28mm |
| Weight | 223.5 g |



Operating System
We compile the eC-Guard platform from source code on Linux, allowing us to maintain hardware agnosticism. This flexibility enables us to tailor our code to the specific hardware preferences of our customers.
For those who prefer to use Swedish-made hardware, we wholeheartedly embrace this choice and adapt our Linux kernel to ensure compatibility and optimal performance on that hardware.
Our commitment to hardware agnosticism and customization ensures that our solution can seamlessly integrate with a wide range of hardware configurations to meet the unique needs of our clients.
Cryptography
eCiceron is part of a Swedish initiative called the Cybernode, the aim of which is to accelerate innovation and research within the cybersecurity field. Within the Cybernode, eCiceron participate in the working group for cryptography. One of the primary responsibilities of this group is to monitor and share insights related to developments and resources within the global cryptography landscape.
With the insights provided by this group, we continually strive to implement current cryptographic solutions with best practices at all times. In the event that security experts in the field recommend changes or updates to our security approach, we promptly adjust our implementations to align with these recommendations.
Our commitment to staying up-to-date and adapting to evolving security standards is paramount in maintaining the highest level of data protection and integrity.
We welcome all inquiries related to cryptographic solutions to meet your requirements and challenge ourselves to deliver the best possible solutions. Your satisfaction is our priority, and we are committed to addressing your cryptographic needs effectively. Please don’t hesitate to reach out with any questions or specific challenges you may have, and our team will be eager to assist you.
eC Guard Security Levels
One configuration of eC-Guard can provide all of the different Security levels at the same time. You can have equipment with different purpose and use your own routines with eC-Guard to meet up the level you need for that device.

Very HIGH Security
Air Gapped Work
eC-Guard information synchronization via USB sharing
HIGH Security
Cable Connected
eC-Guard cable connected to End Device
Normal Security
Wi-Fi connected (SSID/PSW rotation)
eC-Guard Wi-Fi connected with strong password WPA3





